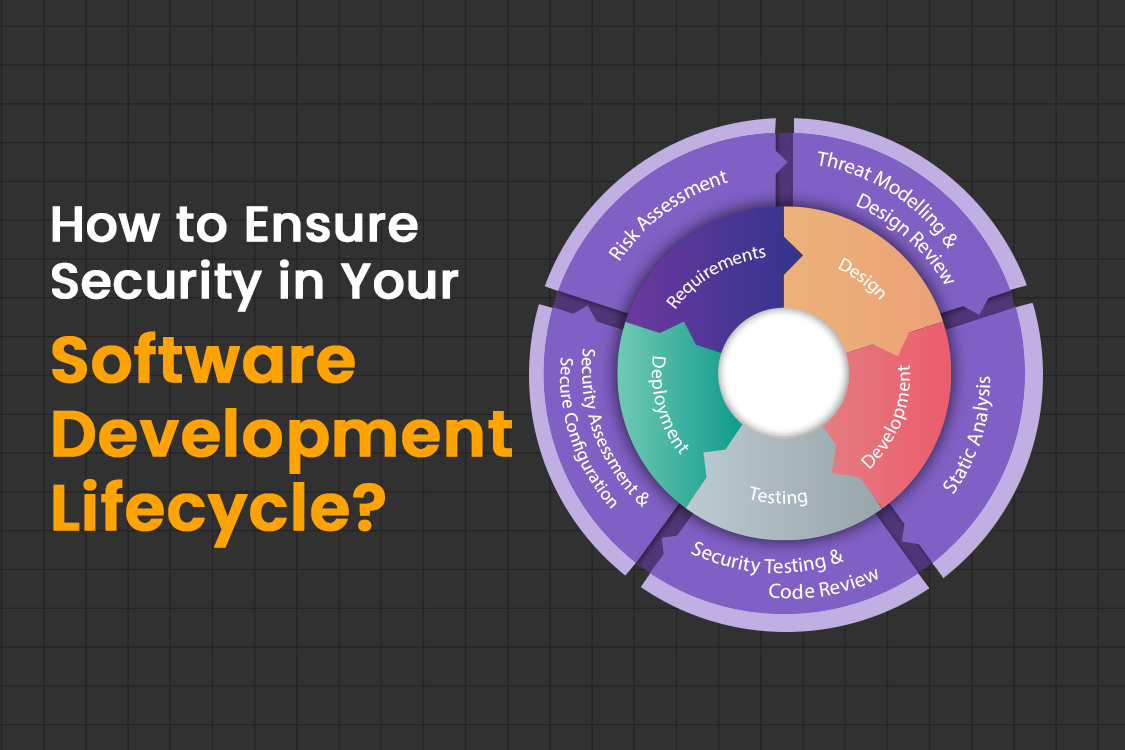
How to Ensure Security in The Software Development Lifecycle?
Security has never been as important as it is in this rapidly moving, digitally-driven world where the vast majority of aspects of our lives are being run by software. It just takes one problem in the software to expose a financial transaction, personal data, or key infrastructure. Implementation of tight security is crucial for each and every part of the Software Development Lifecycle (SDLC). Let us witness the integration of security into every phase to achieve resilient and trustworthy software:
Security-focused vision:
The path to secure software begins a long time before coding starts. At this stage of planning, it is important to set up a vision that prioritizes security for the project. Engage with stakeholders in discussions regarding security requirements and prioritize them over compliance needs and threats. Early attention to these aspects creates a security blueprint for the entire development process.
Companies should also integrate risk assessment to determine any potential issues associated with the systems. This step helps a person know the measures of security required to align their goals based on the perils of the real world.
Security and the outline phase:
Security considerations should be an integral part of the outline phase. This is because a well-structured design can prevent most problems in security from ever happening. Work out the probable threats and vulnerabilities regarding the application. This shall include thinking about the possibility of a hacker misusing a weakness and then measuring the creation of countermeasures.
This could be done by employing several secure design principles, which involve methods such as the principle of least privilege, depth in defense, and security by design. All these system design techniques make them hard to attack and may probably reduce any damage that may be caused. Devise a strategy for both data-at-rest and in-transit encryption, providing mechanisms for the secure processing of information and storage of sensitive information.
Safe and secure programming:
The universality of security should be witnessed during the development phase itself. Check security programming practices against the industry-accepted standard. This shall include input validation, avoidance of hard-coded secrets, gracious capture of all errors to avoid information leakage, and periodic peer reviews of code that might catch security blunders very early in the cycle. Design a security ownership culture in which every one is conscious about their potential security concerns.
Static analysis tools can be run against the code to check for any fallacies before runtime. On the other hand, dynamic analysis seeks runtime errors by actually testing the application.
Testing the security of the software:
Testing is one of the stages where security oversights that may have slipped through earlier phases are identified and solved. Penetration testing is conducted to provide a simulation of attacks similar to real-world scenarios and to identify the potential exploitation of security measures and their weaknesses. Automated security testing tools are used to scan for any configuration problems.
It is vital to include security testing in the pipeline of continuous integration and continuous deployment to make sure that every change is checked for security risks before hitting production.
Launching and deployment:
Placing an application in a live environment brings its own setbacks associated with security. Configure your deployment environment securely and directly, including security patching, hardening of servers, and management of access controls.
Monitoring and logging allow the identification of suspicious activities and the ability to react to threats in near real-time. Review logs for identifying security incidents and responding to them. A clear incident response plan should be documented. It must specify the procedure to be followed during a security breach for containing, assessing the impact, and communicating with the stakeholders.
Updating and Maintenance:
Security does not end here; deploying software is just the beginning. Maintenance is needed to keep your software secure. This would run processes like patch management, which consists of the rapid application of patches against known issues. Train users regarding good security practices and the risks. Awareness protects against malware attacks and other user-directed attacks.
Conclusion:
By having a security vision during the planning phase and being cautious regarding security during design, development, testing, deployment, and maintenance, companies can easily minimize the possibility of security breaches significantly. Finally, security in each of those phases is not just the simple application of certain tools and practices, but implementing them efficiently. That's how companies, by doing so, can protect themselves from all possible threats and amplify trust in users and stakeholders for the safe and successful journey of the software.